About me
I'm Brian, also known as java, an experienced software engineer from Ireland with a passion for C#, C++, reverse engineering, and cybersecurity, focused on building scalable, high-performance tools and applications.
Projects
- fivem-parking - Game-ready, server-side vehicle garage system designed for realism.
- deploy - Utility tool used for managing fixes, changes, and updates to a specific environment.
- sprite3 - Utility tool used for working with 3D models and other GTAV-related assets.
- mem-scope - Utility tool used for reverse engineering UE-based games.
- samp-gm7 - Comprehensive player and game state manager for a samp gamemode.
- prisma - Utility tool used for showcasing examples of how to utilize Prisma ORM within Cfx.re (FiveM).
- fivem-attributes - Game-ready, server-side character attributes system inspired by samp.
- fivem-paynspray - Game-ready, server-side network of basic vehicle repair shops inspired by samp.
- fivem-airsoft - Game-ready. server-side airsoft combat system featuring 1v1 duels and team-based battles.
- fivem-graffiti - 3D graffiti system supporting wall and object tagging with visual persistence.
- fivem-infomarkers - Game-ready, standalone information marker system to generate data points similar to a "scene".
- fivem-arcade - Game-ready, interactive arcade system with multiple mini-games.
- sc - Realistic speed camera system for RAGEMP to prevent players constantly speeding through high-traffic areas.
- fs - Realistic fishing system with a built-in minigame for RAGEMP to make the activity more interactive for players.
- shivi - Utility tool used for handling moderation and security tasks via Discord.
- launcher - GUI-based game launcher for connecting to specific Cfx.re (FiveM) and RAGEMP servers.
- vanity - Utility tool used for assigning roles based on user statuses via Discord.
Note: This is just a small portion of my work that I felt like sharing. Most of these repositories have been made private due to exclusivity or because they were created as part of commissioned work.
XOR Packet Verification in GOW (Gears of War)
In this post, I will talk about how I found a critical vulnerability in Gears of War's multiplayer networking, rooted in its native UObject system and replication framework.
This exploit allowed malicious attackers to inject forged packets that could trigger server-side events without proper authentication, replaying of captured packets to repeat one-time actions, and real-time manipulation of replicated actor properties.
What is Gears of War?
Gears of War is a third-person shooter developed by TC (The Coalition) and Epic Games, built on Unreal Engine 3.
The game's multiplayer system relies heavily on UE3's replication layer—a networking framework designed to synchronize actors, variables, and gameplay events between clients and the server. This system automatically propagates state changes to connected players.
First thought
After dumping the game, I used UE3-specific analysis tools to map key structures such as UObject and identify core replication functions, along with UE3-specific type libraries for UObject and FName parsing.
I then used a small dynamic memory introspection tool to extract the GObjects and GNames arrays.
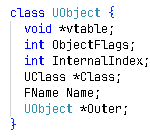
From there, I targeted UObject::ProcessEvent, the core function responsible for dispatching native and UScript calls. Using a signature, I mapped out the base UObject structure:
I located a function responsible for verifying packet integrity. This function implements a simple XOR checksum:
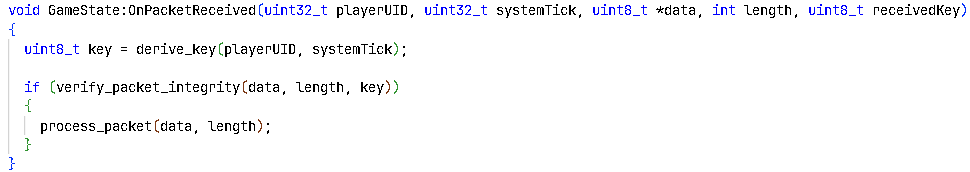
The checksum key is derived by XORing the player's UID with the system tick count, then taking the least significant byte. Since both values are predictable or observable, the key can be easily guessed. Combined with the limited 256 possible XOR checksum values, we can forge packets that pass the integrity check, allowing modification and injection of arbitrary data.
With a reliable write-what-where primitive in place, the next step was to modify and inject arbitrary data by routing all multiplayer packets through a custom proxy. There, I intercepted legitimate packets, removed their checksums, recalculated them using the static XOR key, and reinjected the forged packets. The server accepted these altered packets without error.
Client-supplied data must never be trusted without strict, server-side validation.
Now what?
This issue has been responsibly disclosed to the TC (The Coalition) team in accordance with their security reporting guidelines, and it was addressed quickly and transparently.
God is great.